10 Best Web Application Penetration Testing Tools Shortlist
Here's my pick of the 10 best software from the 18 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
With so many different web application penetration testing tools available, figuring out which is right for you is tough. You know you want to uncover and assess security weaknesses in your web applications but need to figure out which tool is best. I've got you! In this post I'll help make your choice easy, sharing my personal experiences using dozens of different web application penetration testing software with various teams and projects, with my picks of the best web application penetration testing tools.
Why Trust Our Web Application Penetration Testing Tool Reviews?
We’ve been testing and reviewing web application penetration testing tools since 2021. As QA software testers ourselves, we know how critical and difficult it is to make the right decision when selecting software.
We invest in deep research to help our audience make better software purchasing decisions. We’ve tested more than 2,000 tools for different use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & our web application penetration testing tool review methodology.
The Best Web Application Penetration Testing Tools Summary
| Tools | Price | |
|---|---|---|
| New Relic | From $49/user/month | Website |
| Astra Pentest | From $199/month | Website |
| Intruder | From $196/month/application | Website |
| AppTrana | $99/month/app | Website |
| Metasploit | Pricing available upon request | Website |
| Wireshark | Free | Website |
| Gobuster | No price details | Website |
| Invicti | Available upon request | Website |
| Core Impact | Starts at $9,450 USD/year for the Basic package | Website |
| Amass | No price details | Website |
Compare Software Specs Side by Side
Use our comparison chart to review and evaluate software specs side-by-side.
Compare SoftwareHow To Choose Web Application Penetration Testing Tools
With so many different web application penetration testing tools available, it can be challenging to make decisions on what tools are going to be the best fit for your needs.
As you're shortlisting, trialing, and selecting web application penetration testing tools, consider:
- What problem are you trying to solve - Start by identifying the web application penetration testing tool feature gap you're trying to fill to clarify the features and functionality the tool needs to provide.
- Who will need to use it - To evaluate cost and requirements, consider who'll be using the software and how many licenses you'll need. You'll need to evaluate if it'll just be the QA software testers or the whole organization that will require access. When that's clear, it's worth considering if you're prioritizing ease of use for all or speed for your web application penetration testing tool power users.
- What other tools it needs to work with - Clarify what tools you're replacing, what tools are staying, and the tools you'll need to integrate with, such as other testing tools, automation tools, or bug tracking software. You'll need to decide if the tools will need to integrate together or if you can replace multiple tools with one consolidated web application penetration testing tool.
- What outcomes are important - Consider the result that the software needs to deliver to be considered a success. Consider what capability you want to gain or what you want to improve and how you will be measuring success. For example, an outcome could be the ability to get greater visibility into performance. You could compare web application penetration testing tool features until you’re blue in the face but if you aren’t thinking about the outcomes you want to drive, you could be wasting a lot of valuable time.
- How it would work within your organization - Consider the software selection alongside your workflows and delivery methodology. Evaluate what's working well, and the areas that are causing issues that need to be addressed. Remember every business is different — don’t assume that because a tool is popular that it'll work in your organization.
Best Web Application Penetration Testing Tool Reviews
Here’s a brief description of each web application penetration testing tool to showcase each tool’s best use case, some noteworthy features, and screenshots to give a snapshot of the user interface.
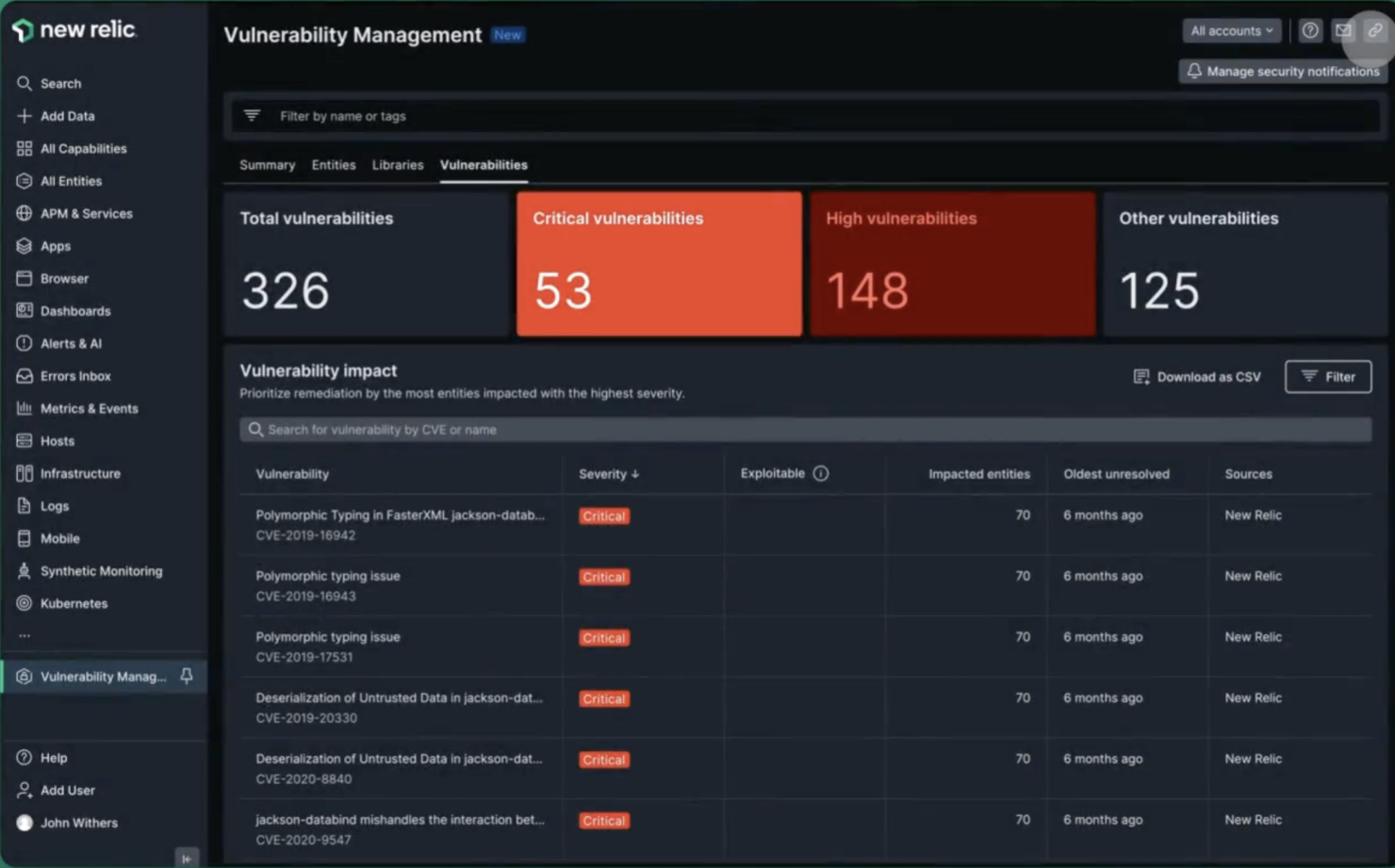
New Relic is a real-time monitoring tool that's designed to help you keep an eye on your app's performance, find out where the bottlenecks are, and fix them before they become a problem.
The platform includes real-time performance monitoring that lets you see exactly how an app is performing in real time so you can spot any issues as they happen and fix them straight away. It also includes detailed analytics, which allow you to drill down into an app's performance data to find out exactly what's going on. And it's all presented in a really easy-to-understand way.
Key features include backend monitoring, Kubernetes monitoring, mobile monitoring, model performance monitoring, infrastructure monitoring, log management, error tracking, network monitoring, vulnerability management, and browser monitoring.
Integrations include over 500 apps, like AWS, Google Cloud, and Microsoft Azure; CI/CD tools like Jenkins, CircleCI, and Travis CI; communication tools like Slack and PagerDuty; and other monitoring and analytics tools like Grafana, Datadog, and Splunk. It also has an API you can use to build custom integrations.
New Relic costs from $49/user/month and offers a free plan for 1 user and 100 GB/month of data ingest.
Best for continuous vulnerability scanning & pentesting for 9300+ test cases
Astra Pentest is a developer-friendly pentest platform featuring an automated vulnerability scanner and manual pentesting by security experts to ensure zero false positives. The platform's vulnerability scanner runs 9300+ test cases covering OWASP, SANS, ISO, SOC, and other standards. This AI-powered business logic test cases feature ensures deep security testing coverage. Additionally, the AI-powered conversational chatbot gives engineers contextual insights on fixing vulnerabilities.
Astra's pentest platform provides a collaborative dashboard that allows team members and security experts to work together efficiently, and it offers a publicly verifiable security certificate to help build trust with customers and partners. The platform also provides real-time support from security experts and emphasizes continuous scanning, which enables ongoing monitoring and detection of security issues.
Furthermore, like the vulnerability scanner, the penetration testing tool covers a wide range of security standards and offers compliance testing for regulations such as ISO 27001, HIPAA, SOC2, and GDPR. The software can also scan progressive web apps, single-page apps, and behind logged-in pages. Integrations include GitHub, GitLab, Slack, Jira, and more.
Paid plans start at $199/month for the Scanner package and they have a free demo available.
Intruder is a vulnerability management tool designed to help businesses identify and address security weaknesses across their digital infrastructure. It provides continuous network monitoring, automated vulnerability scanning, and proactive threat response, which collectively contribute to a more secure IT environment for companies aiming to minimize their attack surface.
I chose this platform for my list because of its automation capabilities. It uses underlying vulnerability scanners to take a proactive approach to vulnerability management. This automated scanning feature allows for regular and systematic vulnerability assessments of digital assets with minimal manual effort. Meanwhile, the tool's continuous monitoring and real-time threat monitoring capabilities ensure that security statuses are always current, adapting to new threats and environmental changes.
The software integrates natively with Slack, Microsoft Teams, Jira, Github, and Gitlab. Other integrations can be accessed through Zapier and API.
Paid plans start from $196 per month, per application. A 14-day free trial is also available.
AppTrana is a web application firewall (WAF) used for penetration testing, behavioral-based DDoS protection, mitigating bot attacks, and defending against the OWASP top 10 vulnerabilities. AppTrana is employed by security-conscious companies across myriad industries, such as Axis Bank, Jet Aviation, Niva Health Insurance, and TRL Transport.
AppTrana is a fully managed security solution, which means that their web security expert team takes on the analyzing and updating of security policies so you don't have to. Higher-level accounts will get a named account manager to assist them; the highest subscription level comes with quarterly service reviews (highly recommended!).
Key features include unlimited application security scanning, manual pen-testing of applications, managed CDN, false positive monitoring, custom SSL certificates, and risk-based API Protection. Their website is packed full of detailed feature explanations as well as a blog, learning center, whitepapers, infographics, and datasheets, so I highly recommend you take a look around for yourself.
AppTrana costs from $99/month/app and comes with a free 14-day trial.
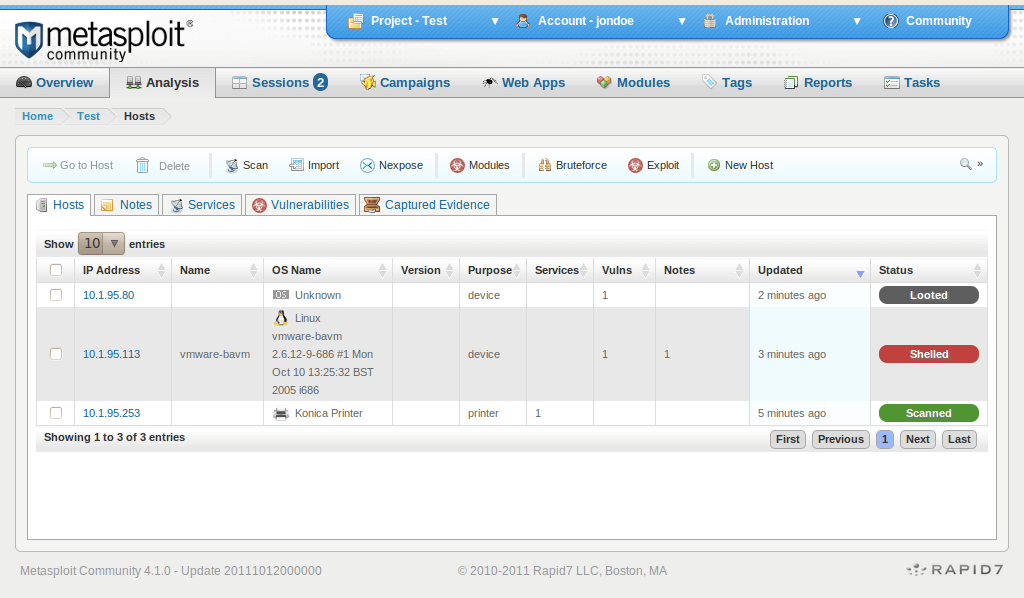
Metasploit is a web application penetration testing tool that identifies system weaknesses and attempts to exploit them, allowing you to isolate and demonstrate the weakness, and allow for remediations. The tool also works across multiple computer systems such as Windows, Linux and Mac OS X, and can be used across devices.
Metasploit provides the ability to automate manual tests and exploits, allowing you to minimize your team’s time spent on creating manual tests and scans. The tool boasts a large exploit database with new additions regularly, and is extremely intuitive, making it easy for you and your team to implement. Metaspolit also has a large community support system.
Metasploit integrates with tools such as Kali Linux and Dradis.
The cost of Metasploit starts at $2,000 per year. The tool also offers a free version.
Network protocol analyzer that is fully open source, and tracks your network and traffic for cyber security
Wireshark is a powerful open source network packet sniffer equipped for the deep inspection of hundreds of different protocols, with more being added all the time. Wireshark runs on multiple platforms, including Windows, macOS, Linux, Solaris, NetBSD, FreeBSD, and many others.Wireshark can read live data from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others in a wide range of file formats. Data can easily be exported, compressed and decompressed for offline analysis, and the platform also has a user-friendly built-in network protocol debugging environment.Wireshark integrates with a wide range of tools, including network software emulators like GNS3.Wireshark is open source and free to use.
Gobuster is a penetration testing tool that is accessible via Github, which allows you to conduct scanning across your web application, and brute force your URIs, DNS subdomains and Virtual Host names on target web servers which allows you to identify unprotected scripts and old configuration files.
Gobuster is hosted on GitHub and can be installed using your terminal. The tool provides the ability to conduct recon tests, which allows you to delve into the depths of your web application and detect vulnerabilities. The tool then provides a thorough report so you can review your code effectively.
Gobuster is fully open source and free to use.
Invicti is an automated security testing tool that allows you and your organization to secure all your web applications and reduce the risk of a cyber attack. Invicti is easy to configure, allows you to scan your websites and web applications for security flaws, and generates results reports. The tool also provides a technology dashboard that shows information about software versions used in your applications.
Invicti allows you to configure pre-set scan profiles, making it easy for anyone in your team to run scans and penetration tests. The feature is entirely customizable so you can set your scan profiles up in a way that is best for your web application. Invicti also has a 24/7 responsive support team.
Inviciti integrates with tools such as Bugzilla, BitBucket and Asana.
Invicti provides customized pricing upon request.
Core Impact is a comprehensive web application penetration testing tool that allows you to exploit weaknesses in the security of your applications, and increase productivity. The tool provides an easy and clean user interface, as well as the ability to execute rapid penetration tests. This allows you to discover, test and report more efficiently.
Core Impact provides a feature for replicating multi-staged attacks, which allows you to pivot your pen tests across various systems, devices and applications. The feature allows you to configure various tests and execute them all at once. Another feature of Core Impact is the ability to install an agent on the server through SSH and SMB, making white box testing more effective.
The cost of Core Impact starts at $9,450 USD per year for the Basic package. The tool also offers a free trial.
Amass is a penetration testing tool that allows you to perform network mapping of cyber attack surfaces, known as Attack Surface Management (ASM). This feature provides continuous monitoring of your changing attack surface, allowing you to ensure your application is covered for various cyber attacks. The tool also provides reporting of the results of these penetration tests.
Amass provides features such as external asset discovery, which allows you to identify and locate active and inactive assets that are unknown to your organization. With the feature, you can monitor the security of your application round-the-clock, and improve your team’s vulnerability management.
Amass is fully open source and free to use.
Other Web Application Penetration Testing Tools
Here are a few more that didn’t make the top list.
- John the Ripper
Penetration testing tool and password cracker which allows you to test the strength of your passwords
- Burp Suite
provides a passive scan feature
- Zed Attack Proxy (ZAP)
Focuses on being the “middleman proxy” between browser and application
- NMap
Lightweight solution to web application penetration testing
- Nessus
Easy to use credential and non credential scans
- Wfuzz
A penetration testing tool specifically for brute-forcing your web applications
- Medusa
An application-based penetration and data testing tool that allows you to execute pen tests for the data and signal integrity of your applications
- SQLMap
An open-source penetration testing tool specifically for detecting and exploiting SQL injection flaws
Related Web Application Penetration Testing Tool Reviews
If you still haven't found what you're looking for here, check out these tools closely related to web application penetration testing tools that we've tested and evaluated.
- Automation Testing Tools
- Software Testing Tools
- Test Management Tools
- CI/CD Tools
- Incident Management Software
- Code Review Tools
Selection Criteria For Web Application Penetration Testing Tools
Selecting the right web application penetration testing tools is a critical process integral to identifying vulnerabilities and ensuring the security of web applications. My approach to choosing these tools is rooted in hands-on experience and a thorough investigation into how each tool performs across various testing scenarios. The right tool should not only possess a robust set of features but also align with the specific use cases and challenges faced by organizations in safeguarding their applications.
Core Web Application Penetration Testing Tool Functionality: 25% of total weighting score
To be considered for inclusion on my list of the best web application penetration testing tools, the solution had to support the ability to fulfill common use cases:
- Identification and exploitation of vulnerabilities like SQL injection, XSS, and CSRF.
- Comprehensive scanning for weaknesses across all layers of the web application.
- Detailed reporting that offers actionable insights and prioritizes vulnerabilities.
- Adaptability to test custom-built as well as standard web applications.
- Ability to integrate within the broader cybersecurity framework of an organization.
Additional Standout Features: 25% of total weighting score
Innovative tools distinguish themselves through:
- Incorporation of machine learning to enhance vulnerability detection and reduce false positives.
- Real-time collaborative testing features for team-based penetration testing activities.
- Advanced automation capabilities that streamline repetitive testing tasks.
- Custom scripting or testing capabilities that allow for tailored assessment strategies.
- Interactive tools that facilitate deep dive manual testing for complex vulnerabilities.
Usability: 10% of total weighting score
Ease of use is essential for:
- Intuitive user interfaces that simplify navigation and accelerate the testing process.
- Clear, organized presentation of findings to aid in quick comprehension and action.
- Configurable settings that cater to various skill levels, from novice testers to experts.
- Accessibility features that ensure the tool is usable by a diverse group of professionals.
Onboarding: 10% of total weighting score
Effective onboarding processes should include:
- Comprehensive documentation and accessible learning resources.
- Supportive onboarding sessions that guide new users through the tool’s functionalities.
- Interactive tutorials or simulations that provide hands-on experience.
- Community forums or support networks that encourage knowledge exchange and troubleshooting.
Customer Support: 10% of total weighting score
Quality customer support is characterized by:
- Prompt and knowledgeable assistance for both technical and user experience issues.
- A variety of support channels tailored to different preferences and needs.
- Proactive engagement and follow-up on user inquiries and feedback.
- Availability of expert guidance for advanced penetration testing challenges.
Value For Money: 10% of total weighting score
When evaluating cost-effectiveness:
- Transparent pricing models that align with the tool's features and capabilities.
- Differentiated pricing plans that cater to various organizational sizes and needs.
- Demonstrable ROI through effectiveness in identifying and mitigating potential breaches.
- Flexibility to upgrade or scale based on evolving testing requirements.
Customer Reviews: 10% of total weighting score
Insights from customer reviews offer:
- Real-world perspectives on the tool’s performance and reliability.
- User experiences that highlight both strengths and areas for improvement.
- Feedback on the long-term value and support provided by the vendor.
- Comparative insights that help gauge the tool’s standing in the market.
In selecting a web application penetration testing tool, aligning its functionalities with your organization's specific security requirements and pain points is crucial. By focusing on comprehensive feature sets, usability, supportive onboarding and customer service, and overall value, you can choose a tool that not only fortifies your web applications but also integrates effectively into your security strategy, ensuring robust defense mechanisms against potential threats.
Trends In Web Application Penetration Testing Tools For 2024
A review of recent product updates, press releases, and release logs from leading web application penetration testing tools in this domain provides valuable insights into current trends and emerging functionalities. Here's a summary highlighting the key developments and what they signify for the industry:
Trends in Web Application Penetration Testing Tools and Technology
- Integration with AI and Machine Learning: Advanced tools are increasingly leveraging AI and ML to enhance testing efficiency, accuracy, and to predict potential security flaws more effectively.
- Evidence: New features in tools that use AI to automate vulnerability detection processes, reducing manual effort and time.
- Emphasis on Automation: There is a growing focus on automating repetitive and time-consuming tasks within the penetration testing process to increase speed and efficiency.
- Evidence: Enhanced capabilities for automated scanning, reporting, and vulnerability assessment.
Rapidly Evolving Features
- Real-time Collaboration: Modern penetration testing tools are incorporating features that facilitate real-time collaboration among team members, allowing for more dynamic and coordinated testing efforts.
- Evidence: Tools now offer shared workspaces and integrated communication channels to enable testers to collaborate effectively.
- Enhanced Reporting and Analytics: There is a significant advancement in how testing tools report and analyze findings, providing deeper insights and actionable intelligence.
- Evidence: Introduction of advanced analytics features that help in understanding the impact of vulnerabilities and prioritizing remediation efforts.
Novel and Unusual Functionality
- IoT and API Security Testing: As IoT devices and APIs become more prevalent, testing tools are expanding their capabilities to address these specific areas, offering more comprehensive testing suites.
- Evidence: New modules and functionalities designed to test the security of IoT ecosystems and API integrations.
Most Important and In Demand Features
- Cloud-Based Testing Environments: The demand for cloud-based penetration testing platforms is rising, offering scalability and flexibility to test web applications in various environments.
- Evidence: An increase in cloud-based platforms that provide on-demand testing environments and integrate with various cloud services.
Features Becoming Less Important
- Standalone Tools: The need for standalone, isolated testing tools is diminishing as integration and interoperability with other cybersecurity tools and frameworks become crucial.
- Evidence: A shift towards tools that offer extensive integration capabilities with other security and development platforms.
The evolution of web application penetration testing tools highlights a shift towards more intelligent, automated, and collaborative approaches, addressing the complex and dynamic nature of modern web applications and cybersecurity threats. For QA software testers, staying updated with these trends is imperative to harness the full potential of these tools, ensuring robust security and compliance in an increasingly digital world.
What Are Web Application Penetration Testing Tools?
Web application penetration testing tools are software used to evaluate the security of web applications. They simulate attacks on the applications to identify vulnerabilities, such as security misconfigurations, weak authentication, and susceptibility to different types of cyber attacks. These tools automate the process of testing, making it systematic and comprehensive.
The benefits of using web application penetration testing tools include the early identification and resolution of security vulnerabilities, which enhances the overall security of the web application. They help in preventing potential data breaches and unauthorized access, thereby safeguarding sensitive information. These tools are essential for maintaining compliance with security standards and regulations. Regular use of these tools builds user trust by ensuring that web applications are robust against cyber threats, and they also aid in making informed decisions about risk management and security strategies.
Features Of Web Application Penetration Testing Tools
In the realm of cybersecurity, web application penetration testing tools are indispensable for uncovering vulnerabilities that could compromise the integrity and confidentiality of web applications. These tools simulate real-world attacks to identify weak spots within applications, enabling organizations to fortify their defenses before malicious actors can exploit them. When selecting a penetration testing tool, it is crucial to consider a range of features that cater to comprehensive testing needs while providing actionable insights. Here are the most important features to look for:
- Comprehensive Scanning Capabilities: Enables thorough scanning of web applications to detect a wide array of vulnerabilities. This feature is essential for identifying potential security issues across various application components.
- Automated Vulnerability Assessment: Offers automated testing processes to identify known vulnerabilities efficiently. Automated assessments help streamline the testing process, allowing testers to focus on more complex tasks.
- Manual Testing Flexibility: Provides functionalities for testers to perform manual, exploratory testing for custom attack simulations. This flexibility is vital for digging deeper into business logic flaws that automated scans might miss.
- Real-Time Reporting and Alerts: Delivers immediate feedback on detected vulnerabilities, facilitating swift action. Timely alerts and detailed reports are crucial for understanding the risk landscape and prioritizing remediation efforts.
- Integration with Development Tools: Allows integration with development and CI/CD tools to embed security testing within the software development lifecycle. Such integration ensures that security is a continuous focus throughout the application development process.
- Support for Latest Technologies: Keeps pace with evolving web technologies, offering testing capabilities for modern frameworks and architectures. Staying current is necessary to effectively test and secure contemporary web applications.
- Customization and Extensibility: Enables testers to tailor testing approaches and extend tool capabilities to suit specific application environments or testing needs. Customization ensures that the tool remains relevant and effective as organizational needs evolve.
- Collaboration Features: Supports team collaboration, enabling multiple testers to work concurrently or share findings. Collaboration tools enhance testing efficiency and knowledge sharing within teams.
- Compliance Checks: Includes features to test against compliance standards and security benchmarks. Ensuring compliance helps organizations meet regulatory requirements and maintain industry best practices.
- User-Friendly Interface: Boasts an intuitive interface that simplifies the complexity of penetration testing for users of varying expertise levels. A user-friendly tool can accelerate the learning curve and enhance productivity.
Selecting a web application penetration testing tool with these features enables organizations to conduct thorough and effective security assessments. By choosing a tool that aligns with these criteria, teams can ensure comprehensive coverage of their web applications' security posture, ultimately safeguarding their digital assets against emerging threats.
Benefits Of Web Application Penetration Testing Tools
For businesses looking to safeguard their digital assets, understanding the key benefits of web application penetration testing tools can guide informed decision-making and investment in the right technology. Here are five primary benefits of web application penetration testing tools:
- Early Detection of Vulnerabilities: These tools proactively identify security weaknesses before they can be exploited by attackers. Early detection is crucial for preventing potential breaches and minimizing the risk of data loss or theft.
- Cost Savings: By identifying and addressing vulnerabilities early, these tools help avoid the significant costs associated with data breaches, including financial losses, legal liabilities, and reputational damage. Investing in penetration testing can result in substantial long-term savings.
- Compliance Assurance: Many tools include features to test against specific compliance standards, helping organizations meet regulatory requirements and avoid penalties. Compliance assurance ensures that businesses operate within legal frameworks and maintain industry standards.
- Enhanced Security Posture: Regular use of penetration testing tools strengthens an organization's security posture by continually identifying and addressing vulnerabilities. This ongoing process helps build a robust defense mechanism against evolving cyber threats.
- Improved Customer Trust: Demonstrating a commitment to security through regular penetration testing can enhance trust with customers and stakeholders. Trust is a critical asset in the digital age, correlating directly with customer loyalty and business reputation.
Costs & Pricing For Web Application Penetration Testing Tools
Choosing the right web application penetration testing tool is a pivotal decision that can significantly influence the security posture of your organization. These tools come in various plans and pricing options, each designed to cater to different organizational sizes, testing frequencies, and depth of analysis required. Understanding the spectrum of available options will empower you to select a tool that not only fits your budget but also aligns with your security objectives. Below is a structured overview of typical plan options you might encounter in the market:
Plan Comparison Table For Web Application Penetration Testing Tools
| Plan Type | Average Price | Common Features Included |
|---|---|---|
| Basic | $20 - $200 per month | Automated scanning, limited scans per month, basic reporting, community support |
| Professional | $200 - $1,000 per month | Advanced scanning capabilities, increased scan limits, detailed reporting, priority support |
| Enterprise | $1,000 - $5,000+ per month | Comprehensive testing suite, unlimited scans, dedicated support, API access, custom features |
| Free | $0 | Access to basic scanning features, very limited scans, community forums for support |
When selecting a web application penetration testing tool, consider the scale of your web presence, the complexity of your applications, and the depth of testing required. Balancing these factors against the available budget will help you choose a plan that effectively bolsters your web application security while providing value for money.
Web Application Penetration Testing Tool Frequently Asked Questions
What Are The Top Penetration Testing Techniques?
There are various aspects of penetration testing that you can use to execute successful security testing.
Black Box Test
Black box pentesting examines the functionality of an application without the need to delve into its internal structures, and can be applied to any stage of software testing.
White Box Test
While black box testing examines the functionality at a high level, white box testing tests the internal structures of a web application including its code, infrastructure and integrations with external platforms.
Network Service Penetration Testing
A network service penetration test identifies security vulnerabilities in your network. The test simulates malicious cases to evaluate the network's cyber security.
Web Application Penetration Testing
A web application penetration test, or pen test, simulates a cyber attack on your web application to identify vulnerabilities in your web application. It is often used to expand a web application's firewall.
Wireless Penetration Testing
Wireless penetration testing identifies and examines connections between all operating devices on one business wifi network.
Social Engineering Penetration Testing
Social engineering penetration testing is the attempt of typical social engineering scams on a business and its employees to determine the level of vulnerability of the organization.
Physical Penetration Testing
Physical penetration testing are tests that attempt to compromise the security of physical barriers such as locks, sensors, intrusion alarms and motion detectors.
Why Should I Use Web Application Penetration Testing Tools?
Using web application penetration testing tools is essential for several compelling reasons, particularly in today's digital landscape where web applications are frequent targets of cyber threats. These tools are designed to proactively identify and address vulnerabilities, providing critical benefits to organizations:
- Identify Security Weaknesses: Penetration testing tools simulate cyber-attacks in a controlled environment, uncovering vulnerabilities that could be exploited by malicious actors. By identifying these weaknesses before attackers do, you can rectify them and strengthen your application's security.
- Protect Sensitive Data: Many web applications handle sensitive user data, including personal and financial information. Penetration testing helps ensure that this data is securely protected, reducing the risk of data breaches that could have severe legal and reputational consequences.
- Maintain Customer Trust: Users expect their data to be handled securely. Demonstrating a commitment to security through regular penetration testing can build trust with your users, which is crucial for customer retention and brand reputation.
- Avoid Financial Losses: Security breaches can result in substantial financial losses due to data theft, regulatory fines, legal fees, and lost business. Investing in penetration testing tools can help avoid these costs by preventing breaches before they occur.
- Compliance with Regulations: Many industries have regulations that require regular security testing of web applications. Using penetration testing tools can help ensure compliance with these regulations, avoiding fines and legal issues.
- Enhanced Security Posture: Regular penetration testing fosters a culture of continuous improvement in security practices, helping organizations stay ahead of emerging threats. It ensures that security measures evolve in tandem with application development, maintaining a robust defense against cyber threats.
Web application penetration testing tools are vital for ensuring the security and integrity of web applications. They provide a proactive approach to identifying vulnerabilities, safeguarding sensitive data, maintaining user trust, achieving regulatory compliance, and enhancing the overall security posture of an organization.
Additional Testing Software Reviews
You might also want to consider:
- Application Performance Management Software
- Mobile App Testing Services
- Static Application Security Testing Tools (SAST)
Conclusion
Penetration testing is a sure way to test the strength of your application security, and the penetration testing tools above could help streamline your processes and reduce the time spent on it while maintaining good quality results. I hope this article helped you decide which tool is right for you and your team so you are better able to manage your cyber security.
For more articles and thought leadership, be sure to subscribe to The QA Lead newsletter.