10 Best SAST Tools Shortlist
Here's my pick of the 10 best software from the 20 tools reviewed.
With so many different static application security testing tools available, figuring out which is right for you is tough. You know you want to detect and fix security issues before your applications go into production but need to figure out which tool is best. I've got you! In this post I'll help make your choice easy, sharing my personal experiences using dozens of different static application security testing software with various teams and projects, with my picks of the best static application security testing tools.
What Are Static Application Security Testing Tools?
Static Application Security Testing (SAST) tools are software that analyze source code, bytecode, or binary code for security vulnerabilities. These tools perform automated scans of the application's code to identify potential security issues, such as coding errors or weaknesses, without executing the code. SAST tools are used predominantly in the early stages of software development.
The benefits and uses of SAST tools include the early detection and resolution of security vulnerabilities, enhancing the security posture of software applications. They help in maintaining code quality and compliance with coding standards, reducing the risk of security breaches in the final product. By integrating into the software development lifecycle, SAST tools enable developers to address security concerns proactively, saving time and costs associated with post-deployment fixes. They are essential in developing secure software applications in today's environment where cybersecurity is a top priority.
Overviews Of The 10 Best Static Application Security Testing Tools
Here’s a brief description of each of the static application security testing tools to showcase each tool’s best use case, some noteworthy features, and screenshots to give a snapshot of the interface.
New Relic is an all-in-one platform for monitoring and managing performance, testing, and security. It provides you with a comprehensive overview of your applications, infrastructure, and customer experience. When it comes to security testing, you can rely on the platform's vulnerability management module.
You can centralize your data with the software's 500+ integrations. This makes for effective security management, because you can identify vulnerabilities and bridge the gap between security and development. An AI assistant (named 'Grok') in the platform can read your telemetry and identify outliers for you. You can also ask Grok questions, and it will find a root cause for an issue and provide you with potential code changes.
New Relic integrates with over 500 apps including AWS, Google Cloud, Microsoft Azure, Jenkins, CircleCI, Travis CI, and Slack. It also has an API you can use to build custom integrations.
New Relic costs from $49/user/month and has a free version available with feature limitations.
GitHub
Makes it easy to record and rewind changes made to code repositories.
GitHub is a tool that provides significant code collaboration with the history of files in the code repository to be easily tracked. While GitHub still makes it possible to upload source code and share it with remote partners, it has evolved by adding robust security features. GitHub has recently strengthened its competencies in security by enabling developers to find and fix security problems in code as they write.
In essence, GitHub’s application security allows teams to find and fix vulnerabilities before code is merged into the repositories. It facilitates the implementation of left-shift security by enabling the incorporation of security analysis into the development workflow. Thanks to CodeQL, GitHub implements real-time code scanning to provide feedback as you write while also integrating the result natively into the developer workflow.
In addition to its enabled-code scanning for repositories, GitHub also allows DevSecOps to schedule code scanning to run each time there is a pull or push request as part of code review.
GitHub provides personal, organizational, and enterprise account tiers. GitHub allows individuals and organizations to own and use an unlimited number of private and public repositories. Individuals and organizations can use either GitHub Free or GitHub Pro accounts. Likewise, organizations can use GitHub Free but to gain more control and features, they must upgrade to GitHub Team or GitHub Enterprise Cloud.
Generally, GitHub bills for advanced security features by requiring you to purchase a license for an enterprise account; specifically, either GitHub Enterprise Cloud or GitHub Enterprise Server. However, these advanced security features remain free for public repositories hosted on GitHub.com.
So, GitHub is free for individuals and organizations. GitHub Team is $44 per user/year for the first 12 months.
GitHub Enterprise comes with a free trial but is billed at $231/user/year for the first 12 months. However, GitHub primarily uses per-user pricing models, so alternatively, you contact GitHub’s sales team for GitHub Enterprise pricing quotes.
Dynatrace is an application and infrastructure monitoring tool that aims to simplify cloud complexity. It leverages its AI-powered platform to automate DevOps and provide intelligent security to deliver software faster and more securely.
Dynatrace offers a broad view of your computing environment along with a seamless digital experience.
Dynatrace is an all-in-one platform but the pricing is based on the individual components of the ecosystem. Digital experience monitoring is priced at $11/month for 10K annual Digital experience monitoring units. Application security monitoring is priced at $15/month for 8GB per host. Infrastructure monitoring is priced at $22/month for 8GB per host. Open Ingestion is priced at $25/month for 100K annual Davis data units. Cloud automation is priced at $0.10/Cloud automation unit. Full-stack monitoring is priced at $74/month for 8GB per host.
Static code analysis made easy with minimal configuration and code health solutions
DeepSource is a sophisticated static analysis platform that provides enterprise-grade shift left security tools. DeepSource emphasis is on making life easier for DevSecOps and QA teams, with its continuous code quality checks. In addition to judiciously tracking the key metrics of code health,
With DeepSource, you can jump right in and start analyzing code without minimal configurations. If automatically formatting your code wasn’t enough, it goes a step further with its Autoflix feature that generates bug fixes so that vulnerabilities don’t end up in production.
DeepSource can be integrated with tools like BitBucket, GitLab, and GitHub. Moreover, DeepSource is flexible and versatile. It can be used as infrastructure-as-code and covers all the major programming languages.
DeepSource uses a per-user pricing plan. However, it is free for small teams and personal accounts.
Seamless end-to-end testing and vulnerability management scanner that keeps the noise low
GuardRails empowers both developers and security teams to keep code secure through continuous protection and seamless experience. It does this by providing high visibility into security issues while keeping background noise low but with high-impact reporting.
GuardRails is seamlessly integrated into the background of workflows. This affords developers little distraction as they can focus on writing the best code. Although it runs security scans quietly in the background, it nonetheless provides notifications in the form of real-time alerts when significant vulnerabilities emerge.
GuardRails increases productivity while keeping code secure. GuardRails enhances version control system integration with platforms like GitHub due to the ease by which it can be installed or integrated into existing repositories.
GuardRails has a free tier geared toward allowing individuals or small teams to kick-start their AppSec journey. Its Standard tier is an expanded suite with more enhanced security for single teams and is priced at $35 per seat/month. The Professional tier offers advanced tools for teams across portfolios and is priced at $55 per seat/month.
GitLab
Open source software development platform with code review, issue tracking, and version control
GitLab empowers users to build modern applications and accelerate digital transformation by embracing automated processes to deliver code faster.
In addition to providing code repository and version control functions, GitLab comes with built-in DevOps workflows such as continuous integration and continuous delivery (CI/CD) pipelines. GitLab boosts developer productivity and collaboration among developers while reducing costs, cycle time, and time to market.
GitLab is free for individual users. Its Premium edition targets customers who want to enhance team productivity and coordination and is priced at $19/user/month. GitLab Ultimate tier is priced at $99/user/month and is designed for organization-wide security, planning, and compliance.
Codiga is a highly scalable static analysis (SAST) tool that enables developers to write faster code. It facilitates left-shift coding philosophy by enabling DevSecOps and QA teams to detect quality defects early in the software development cycle. Codiga allows you to automate your code reviews with code analysis supported by context-based suggestions.
It boosts productivity, especially for developers who work on multiple computers and platforms, by making all their code snippets easily available. Moreover, Codiga’s Coding Assistant allows developers to write, reuse, and share code snippets directly from their IDE with other team members instead of engaging in their manually arduous task of searching for it.
Meanwhile, Codiga’s Automated Code Review immediately discovers and identifies vulnerabilities and coding problems during pull requests. In addition to capturing bad coding practices such as code duplicates and complex functions, it also reports outdated dependencies as reflected by CVE lists.
In addition to automated testing features, Codiga also provides source coding scanning, workflow management, quality assurance, application security, collaboration tools, and so on. Codiga is also a continuous integration tool for CI pipelines.
Codiga has a free version which is ideal for open-source developers. However, Teams is its priced tier costing $14/month for software engineering teams.
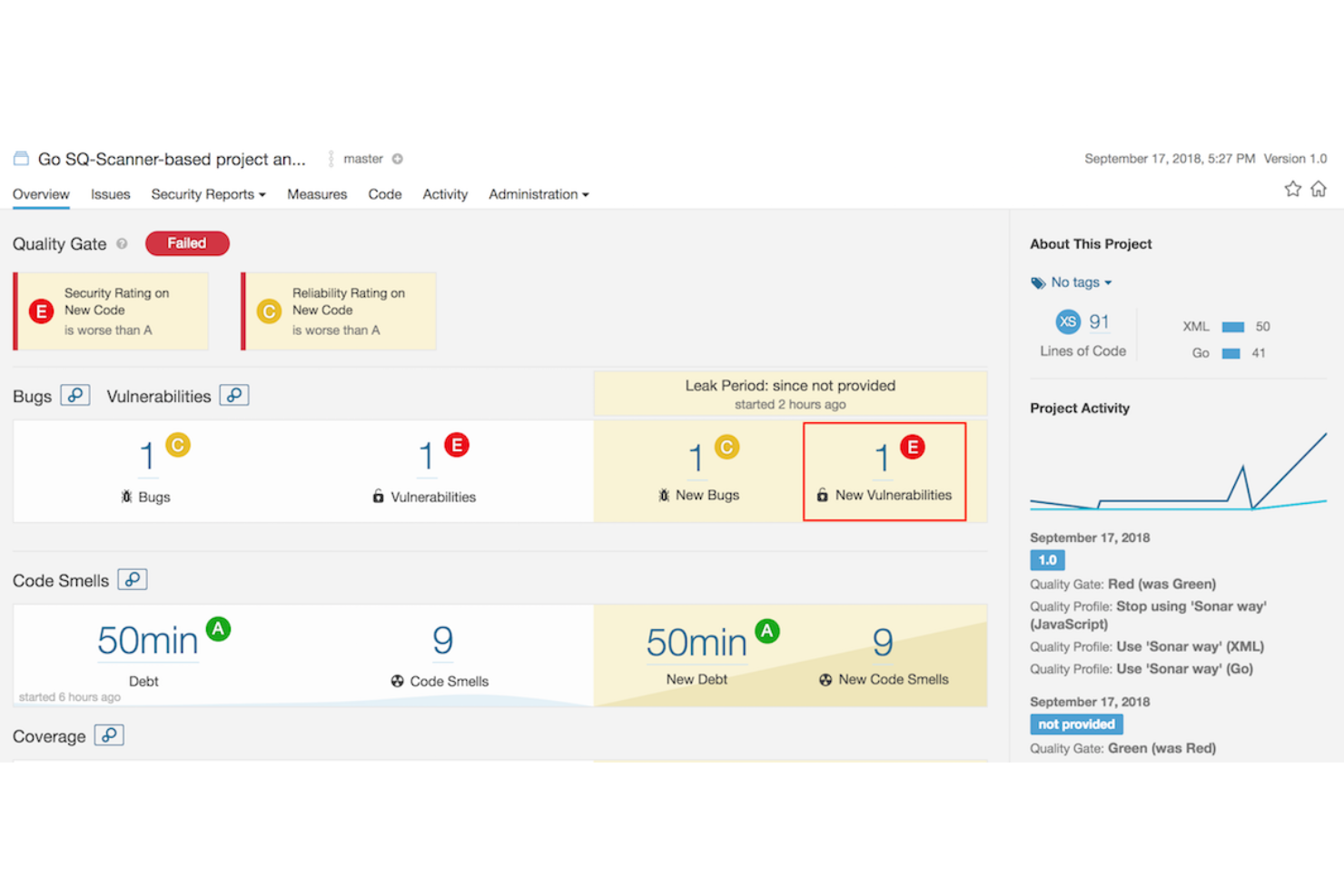
SonarQube puts developers in the position to write safer and cleaner code by automating code inspection. It additionally boosts the process of releasing quality code with the capacity to define static code analysis rules.
SonarQube is versatile and expansive, with support for multi-language applications, which currently stands at 24 programming languages. Some of the vital languages it provides critical security for include C#, C++, Java, PHP, Python, and so on. Moreover, it provides code review feedback by analyzing branches of repositories during pull requests for GitHub, BitBucket, GitLab, and so on.
SonarQube provides developers with multiple points of integration into the software development ecosystem. It offers in-IDE integration with SonarLint while also providing integration into the development and CI/CD workflow. In terms of tools, SonarQube integrates with DevOps tools like Azure DevOps, GitHub, and Jenkins.
SonarQube’s Community edition is open source and free. It includes a 14-day free trial for its Developer, Enterprise, and editions. Pricing for these is also available upon request and appears to be largely contingent on prospective lines of code to be inspected.
Brings API security testing and application security closer to the Developer
StackHawk simplifies and automates application security testing for DevSecOps in CI/CD pipelines. It is a modern dynamic application security testing tool built for developers to uncover and fix vulnerabilities.
StackHawk scans for security vulnerabilities, whether stemming from open-source components or bugs inadvertently introduced into source code. It empowers developers with alerts and sufficient context so they can triage and identify the root cause of the code or security flaw.
With API security testing and integration capabilities, StackHawks works with CI/CD pipelines and DevOps tools such as Jenkins, Travis CI, GitLab, GitHub Actions, CircleCI, Azure Pipelines, BitBucket Pipelines, Atlassian Bamboo, and much more.
StackHawks has a free version for a single application. Others have a 14-day free trial. Its Pro tier is priced at $35/developer/month. The Enterprise tier costs $49/developer/month.
AppSonar specializes in finding hidden security bugs and automates static application testing. It provides flexible approaches to creating scalable quality software by finding bugs faster. AppSonar operates as a standalone application that can be run on either Windows or Linux systems. It can also either be used from the command line or GUI interface.
One of the ways it does this is by empowering users to expand code testing coverage with custom extensions. In addition to providing a gateway to AppSonar functionality, AppSonar extensions are also easy to implement. Instead of creating custom extensions, you can simply download existing ones.
AppSonar’s features include multi-language scanning, deployment management, dashboard interface, debugging, application security, vulnerability, and source code scanning. In addition to IDE integration, AppSonar also easily integrates at any point in the CI/CD pipeline.
AppSonar supports three licensing models. One license follows an annual per-user price of $395. Another has a more limited time window with a license based on 45 days per user for $195. Contact AppSonar’s sales teams for a quote on Enterprise-Wide licensing.
The Best Static Application Security Testing Tools Summary
| Tools | Price | |
|---|---|---|
| New Relic | From $49/user/month | Website |
| GitHub | Starts at $3.67/user/month | Website |
| Dynatrace | From $0.08/8 GB/Hour | Website |
| DeepSource | Free for small teams and personal accounts | Website |
| GuardRails | From $35 per seat/month | Website |
| GitLab | From $19/user/month | Website |
| Codiga | From $14/month for software engineering teams | Website |
| SonarQube | From $20,000/year | Website |
| StackHawk | From $35/developer/month | Website |
| Flawnter | From $195/user/45 days | Website |
Compare Software Specs Side by Side
Use our comparison chart to review and evaluate software specs side-by-side.
Compare SoftwareOther SAST Tool Options
Here are a few more SAST tools that didn’t make the list but are worth checking out.
- Mend SAST
Emphasizes speed without sacrificing security in enterprise application development
- IDA Pro
Interactive disassembler and binary code analysis tool for in-depth code behavioral insight
- Nexus Lifecycle
Provides a single tool to automate supply chain management throughout the SDLC lifecycle
- Codacy
DevOps intelligence platform with high-quality code on 40+ programming languages.
- Klocwork
Static code analysis and SAST tool for C, C++, C#, Java, JavaScript, Python, and Kotlin.
- Brinqa
Consolidate, prioritize and manage findings from all your AST tools.
- LGTM.COM
Free SAST tool for open source projects.
- Reshift
Code security tool that secures your code as you build
- Veracode
Integrate automated AppSec testing into your CI/CD pipeline.
- SpectralOps
Advanced AI backed technology with over 2000 detectors to discover and classify your data silos and uncover data breaches.
Comparison Criteria
What do I look for when I select the best static application security testing tool? Here’s a summary of my evaluation criteria:
- User Interface (UI): The ability of the UI to provide intuitive guidance, so users can discover vital application elements and capture nuance in testing results.
- Usability: This includes ease of use and configuration setup, with a preference for tools that are available as a plugin so developers can integrate and use them unobtrusively into their IDEs.
- Integrations: Workflow integration is vital for SAST tools because they are hardly designed to function as self-contained, standalone applications. To maximize their purpose, they need to provide API integration endpoints.
- Support for major languages: The best SAST tools are versatile and can scan for security vulnerabilities in multiple programming languages, especially those that developers commonly use.
- Scalability: In addition to accommodating several languages, a SAST platform should scale and perform effectively when required to execute lots of software scans.
- Reliably identify known vulnerabilities: A good SAST tool should competently detect and identify well-known threats like code injection flaws, buffer overflow scenarios in code, and those in the OWASP Top Ten.
- Reverse Engineer Binaries: One of the advantages of white box testing is access to the underlying software code and framework. While enhancing the ability to understand the logic of source code, SAST also needs to provide the ability to test from the inside out by discerning binaries and reverse engineering assembly language code.
- Value for $: At a minimum, a tool should be cost-effective. Ideally, it should surprise customers by providing them with exceeding value for the money they pay.
How Do I Use SAST Tooling?
As a white box testing methodology, SAST should be used as early and often as possible in the software development cycle. For those that require a significant learning curve, training should be provided to bring the developers up to speed on how to use it.
What are SAST Tooling Key Features?
Here are the key features I look for when selecting static application security testing tools:
- Bug tracking: The ability to provide issue and bug-tracking capabilities is a vital function of an AppSec tool. This allows DevSecOps to account for the volume of vulnerabilities in the source code and then apply remediation actions.
- Real-time analytics and reporting: These dual features provide QA and cybersecurity with deep insight and visibility into what is happening inside the code. Analytics provides an overview of the logic and execution paths followed by an application while up-to-date reporting adequately documents vulnerability findings.
- Vulnerability scanning: The focal point of any SAST tool is vulnerability scanning to discover flaws in software that may not be easily discernible due to the sheer amount of source code.
- Performing multiple types of code analysis: A good SAST platform shouldn’t be a one-trick pony. To effectively serve customers, it should be able to perform a broad range of analyses including structural analysis, configuration analysis, control flow analysis, data flow analysis, and semantic code analysis.
Other App Testing Software Reviews
You might also want to consider:
- Application Performance Management Software
- Mobile App Testing Services
- Web Application Penetration Testing Tools
What Do You Think About This List?
Kindly subscribe to our newsletter to get the latest insights from thought leaders. You can also discover other things in the QA world, including similar tool comparisons on our site.